 Arbitrum Nova
Arbitrum Nova
Badges
About
Arbitrum Nova is an AnyTrust Optimium, differing from Arbitrum One by not posting transaction data onchain.
Badges
About
Arbitrum Nova is an AnyTrust Optimium, differing from Arbitrum One by not posting transaction data onchain.
ArbOS 32 Emergency upgrade
2024 Sep 25th
SecurityCouncil emergency upgrades to fix attack vectors related to Stylus resource pricing.
Funds can be stolen if
Funds can be lost if
Users can be censored if
MEV can be extracted if
Sequencer failure
Self sequenceState validation
Fraud proofs (INT)Fraud proofs allow actors watching the chain to prove that the state is incorrect. Interactive proofs (INT) require multiple transactions over time to resolve.
Data availability
External (DAC)Proof construction relies fully on data that is NOT published onchain. There exists a Data Availability Committee (DAC) with a threshold of 5/6 that is tasked with protecting and supplying the data.
Exit window
7dNon-emergency upgrades are initiated on L2 and go through a 8d delay. Since there is a 1d delay to force a tx (forcing the inclusion in the following state update), users have only 7d to exit.
If users post a tx after that time, they would only be able to self propose a state root 12d 17h after the last state root was proposed and then wait for the 6d 8h challenge window, while the upgrade would be confirmed just after the 6d 8h challenge window and the 3d L1 timelock.
Proposer failure
Self proposeAnyone can become a Proposer after 12d 17h of inactivity from the currently whitelisted Proposers.
Data is not stored on chain
Users transactions are not published onchain, but rather sent to external trusted parties, also known as committee members (DAC). Members of the DAC collectively produce a Data Availability Certificate (comprising BLS signatures from a quorum) guaranteeing that the data behind the new transaction batch will be available until the expiry period elapses (currently a minimum of two weeks). This signature is not verified by L1, however external Validators will skip the batch if BLS signature is not valid resulting. This will result in a fraud proof challenge if this batch is included in a consecutive state update. It is assumed that at least one honest DAC member that signed the batch will reveal tx data to the Validators if Sequencer decides to act maliciously and withhold the data. If the Sequencer cannot gather enough signatures from the DAC, it will “fall back to rollup” mode and by posting the full data directly to the L1 chain. The current DAC threshold is 5 out of 6.
Funds can be lost if the external data becomes unavailable (CRITICAL).
Users can be censored if the committee restricts their access to the external data.
Set of parties responsible for signing and attesting to the availability of data.
There are no onchain assets at risk of being slashed in case of a data withholding attack. However, there is indirect economic security derived by the committee members being publicly known, and their reputation is at stake should they behave maliciously.
There is no fraud detection mechanism in place. A data withholding attack can only be detected by nodes downloading the full data from the DA layer.
For regular updates, there is a 17d 8h delay before the bridge implementation update is completed. The Security Council can upgrade the DA bridge without delay.
The relayer role is permissioned, but the DA bridge has a Security Council or a governance mechanism to propose new relayers. In case of relayer failure, the DA bridge liveness can be restored by proposing a new relayer after a delay of 17d 8h via governance upgrade, or through a Security Council without delay.
Architecture

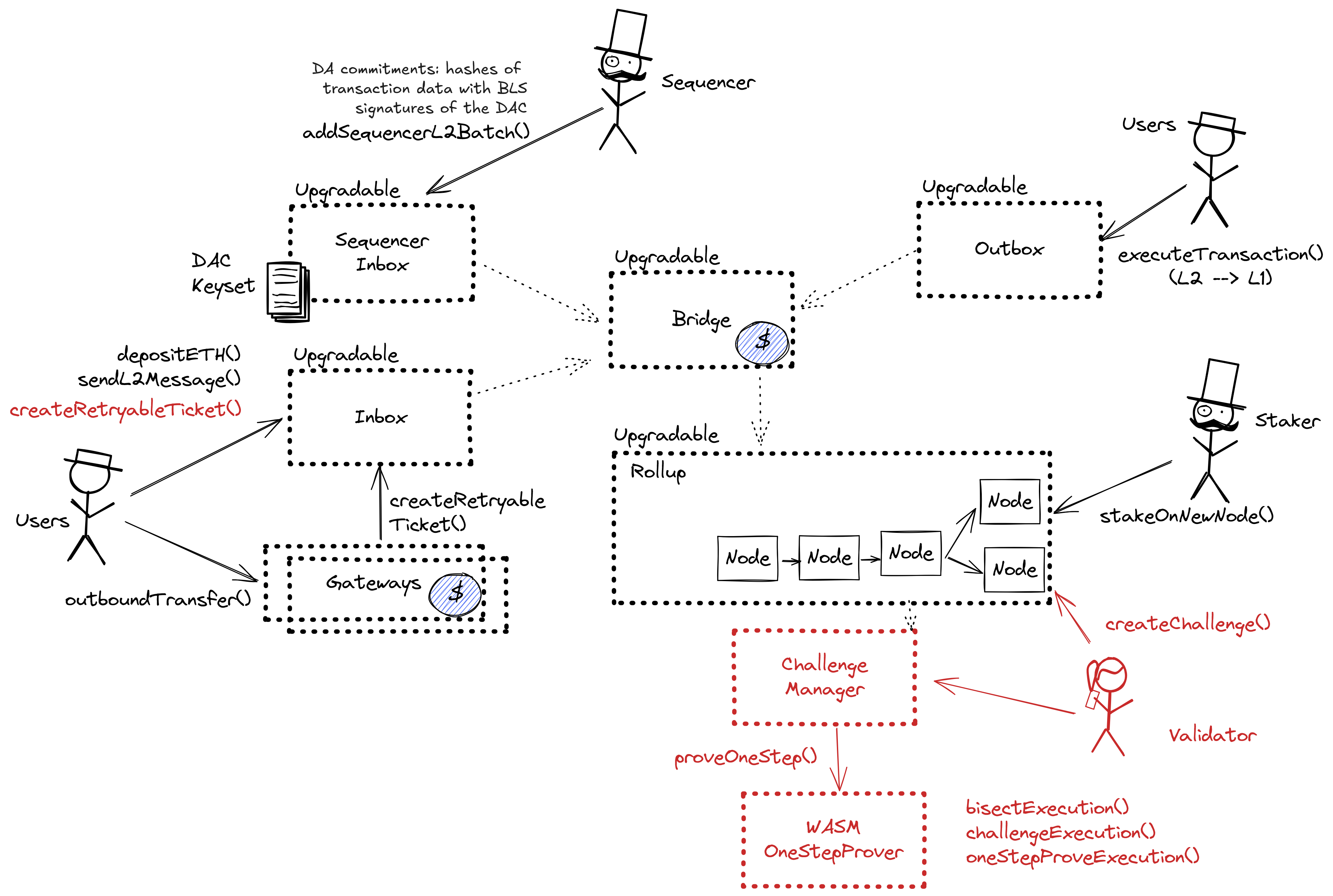
Nova is a data availability solution for Arbitrum rollups built on the AnyTrust protocol. It is composed of the following components:
- Sequencer Inbox: Main entry point for the Sequencer submitting transaction batches.
- Data Availability Committee (DAC): A group of members responsible for storing and providing data on demand.
- Data Availability Certificate (DACert): A commitment ensuring that data blobs are available without needing full data posting on the L1 chain.
Committee members run servers that support APIs for storing and retrieving data blobs. The Sequencer API allows the rollup Sequencer to submit data blobs for storage, while the REST API enables anyone to fetch data by hash. When the Sequencer produces a data batch, it sends the batch along with an expiration time to Committee members, who store it and sign it. Once enough signatures are collected, the Sequencer aggregates them into a valid DACert and posts it to the L1 chain inbox. If the Sequencer fails to collect enough signatures, it falls back to posting the full data to the L1 chain.
A DACert includes a hash of the data block, an expiration time, and proof that the required threshold of Committee members have signed off on the data. The proof consists of a hash of the Keyset used in signing, a bitmap indicating which members signed, and a BLS aggregated signature. L2 nodes reading from the sequencer inbox verify the certificate’s validity by checking the number of signers, the aggregated signature, and that the expiration time is at least two weeks ahead of the L2 timestamp. If the DACert is valid, it provides a proof that the corresponding data is available from honest committee members.
DA Bridge Architecture

In Nova architecture, the DA commitments are posted to the L1 through the sequencer inbox, using the inbox as a DA bridge. The DA commitment consists of Data Availability Certificate (DACert), including a hash of the data block, an expiration time, and a proof that the required threshold of Committee members have signed off on the data. The sequencer distributes the data and collects signatures from Committee members offchain. Only the DACert is posted by the sequencer to the L1 chain inbox (the DA bridge), achieving L2 transaction ordering finality in a single onchain transaction.
DA Bridge Upgradeability

The Arbitrum DAO controls Arbitrum Nova through upgrades and modifications to their smart contracts on Layer 1 Ethereum and the Layer 2s. Regular upgrades, Admin- and Owner actions originate from either the Arbitrum DAO or the non-emergency (proposer-) Security Council on Arbitrum One and pass through multiple delays and timelocks before being executed at their destination. Contrarily, the three Emergency Security Council multisigs (one on each chain: Arbitrum One, Ethereum, Arbitrum Nova) can skip delays and directly access all admin- and upgrade functions of all smart contracts. These two general paths have the same destination: the respective UpgradeExecutor smart contract. Regular upgrades are scheduled in the L2 Timelock. The proposer Security Council can do this directly and the Arbitrum DAO (ARB token holders and delegates) must meet a CoreGovernor-enforced 5% threshold of the votable tokens. The L2 Timelock queues the transaction for a 3d delay and then sends it to the Outbox contract on Ethereum. This incurs another delay (the challenge period) of 6d 8h. When that has passed, the L1 Timelock delays for additional 3d. Both timelocks serve as delays during which the transparent transaction contents can be audited, and even cancelled by the Emergency Security Council. Finally, the transaction can be executed, calling Admin- or Owner functions of the respective destination smart contracts through the UpgradeExecutor on Ethereum. If the predefined transaction destination is Arbitrum One or -Nova, this last call is executed on L2 through the canonical bridge and the aliased address of the L1 Timelock. Operator roles like the Sequencers and Validators are managed using the same paths. Sequencer changes can be delegated to a Batch Poster Manager.
The information in the section might be incomplete or outdated.
The L2BEAT Team is working to research & validate the content before publishing.
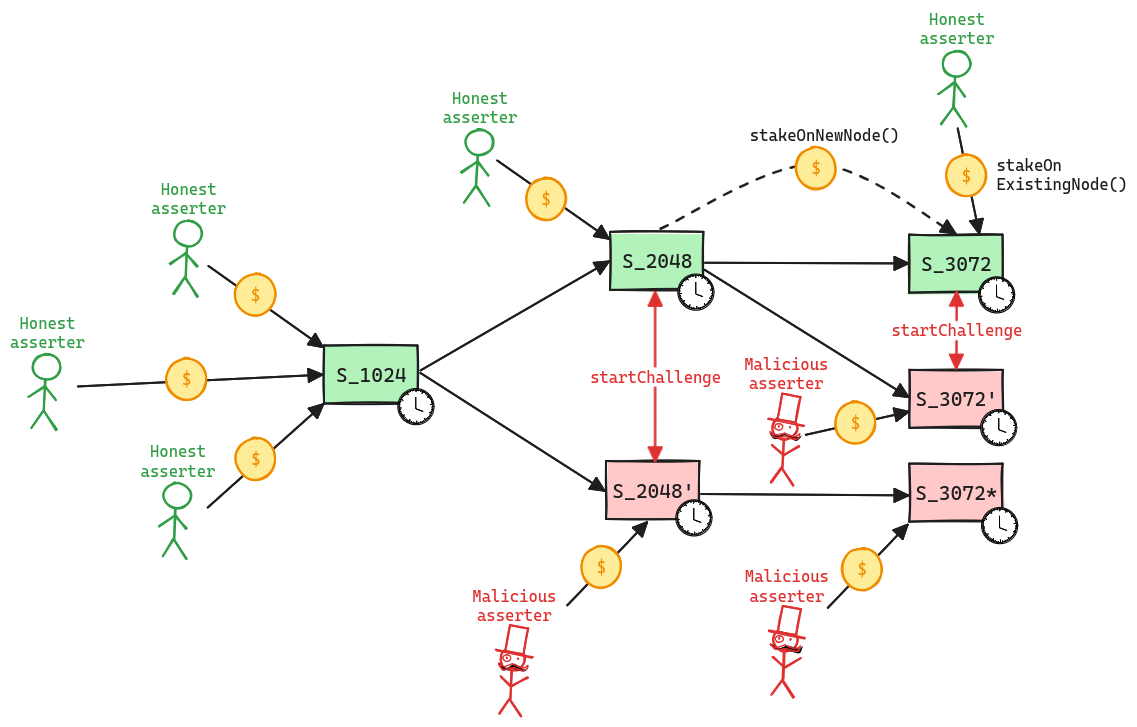
.
The system has a centralized sequencer
While forcing transaction is open to anyone the system employs a privileged sequencer that has priority for submitting transaction batches and ordering transactions.
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction
Because the state of the system is based on transactions submitted on the underlying host chain and anyone can submit their transactions there it allows the users to circumvent censorship by interacting with the smart contract on the host chain directly. After a delay of 1d in which a Sequencer has failed to include a transaction that was directly posted to the smart contract, it can be forcefully included by anyone on the host chain, which finalizes its ordering.
Regular messaging
Autonomous exit
Users can (eventually) exit the system by pushing the transaction on L1 and providing the corresponding state root. The only way to prevent such withdrawal is via an upgrade.
EVM compatible and Stylus smart contracts are supported
Arbitrum One supports smart contracts written in Solidity and other programming languages (Rust, C++) that compile to WASM. Such smart contracts are executed by nodes using either a geth fork or a fork of wasmer inside the Nitro node, and can be proven with the onchain WASM VM.
Funds can be lost if there are mistakes in the highly complex Nitro and WASM one-step prover implementation.
Arbitrum DAO is in charge of upgrades
Arbitrum DAO allows $ARB token holders to propose and vote on changes to the organization and the technologies it governs. The governance smart contracts are implemented on Arbitrum One rollup chain. The DAO can upgrade the Arbitrum One contracts on L2 with 8d delay and - using L2 --> L1 Governance Relay, update contracts on L1 with additional 3d delay + 6d 8h delay for all L2 --> L1 messages (in total a delay of 17d 8h). The Security Council can upgrade the contracts without any delay. It can also cancel any upgrades initiated by the DAO.
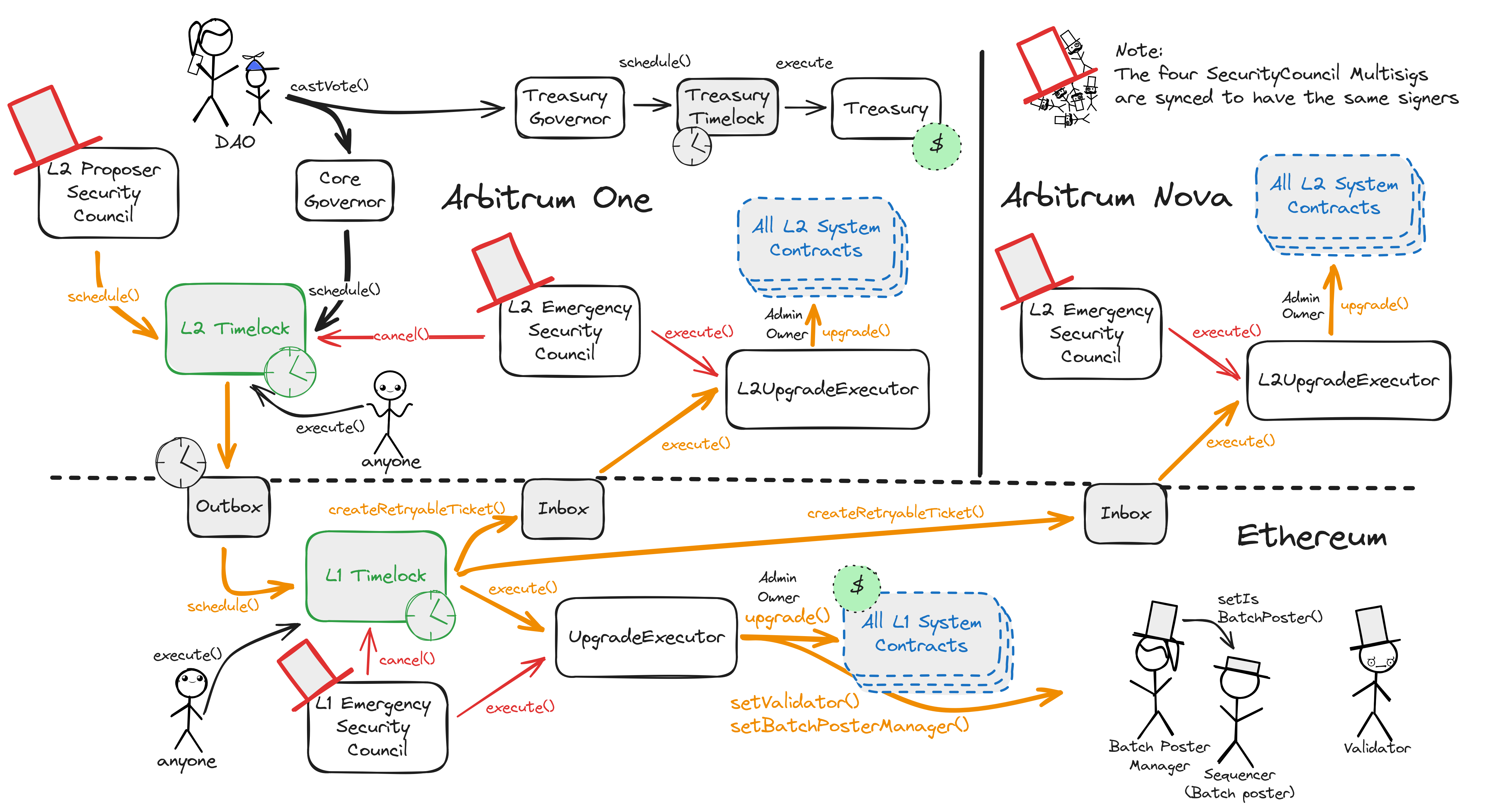
All critical system smart contracts are upgradeable (can be arbitrarily changed). This permission is governed by the Arbitrum Decentralized Autonomous Organization (DAO) and their elected Security Council. The Arbitrum DAO controls Arbitrum One and Arbitrum Nova through upgrades and modifications to their smart contracts on Layer 1 Ethereum and the Layer 2s. While the DAO governs through token-weighted governance in their associated ARB token, the Security Council can directly act through the Security Council smart contracts on all three chains. Although these multisigs are technically separate and connect to different target permissions, their member- and threshold configuration is kept in sync by a manager contract on Arbitrum One and crosschain transactions.
Regular upgrades, Admin- and Owner actions originate from either the Arbitrum DAO or the non-emergency (proposer-) Security Council on Arbitrum One and pass through multiple delays and timelocks before being executed at their destination. Contrarily, the three Emergency Security Council multisigs (one on each chain: Arbitrum One, Ethereum, Arbitrum Nova) can skip delays and directly access all admin- and upgrade functions of all smart contracts. These two general paths have the same destination: the respective UpgradeExecutor smart contract.
Regular upgrades are scheduled in the L2 Timelock. The proposer Security Council can do this directly and the Arbitrum DAO (ARB token holders and delegates) must meet a CoreGovernor-enforced 5% threshold of the votable tokens. The L2 Timelock queues the transaction for a 8d delay and then sends it to the Outbox contract on Ethereum. This incurs another delay (the challenge period) of 6d 8h. When that has passed, the L1 Timelock delays for additional 3d. Both timelocks serve as delays during which the transparent transaction contents can be audited, and even cancelled by the Emergency Security Council. Finally, the transaction can be executed, calling Admin- or Owner functions of the respective destination smart contracts through the UpgradeExecutor on Ethereum. If the predefined transaction destination is Arbitrum One or -Nova, this last call is executed on L2 through the canonical bridge and the aliased address of the L1 Timelock.
Operator roles like the Sequencers and Validators are managed using the same paths. Sequencer changes can be delegated to a Batch Poster Manager.
Transactions targeting the Arbitrum DAO Treasury can be scheduled in the 3d Treasury Timelock by meeting a TreasuryGovernor-enforced 3% threshold of votable ARB tokens. The Security Council cannot regularly cancel these transactions or schedule different ones but can overwrite them anyway by having full admin upgrade permissions for all the underlying smart contracts.
The DA committee has the following members:
Ethereum
Roles:
Can submit transaction batches or commitments to the SequencerInbox contract on the host chain.
Can propose new state roots (called nodes) and challenge state roots on the host chain.
Actors:
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
- Contract used to relay governance action messages from Arbitrum One to Ethereum. It is also an escrow contract for the project’s gas token (can be different from ETH). Keeps a list of allowed Inboxes and Outboxes for canonical bridge messaging.
- Can act on behalf of L1Timelock with 3d delay.
- Is allowed to interact with L1Timelock - cancel queued transactions - acting via UpgradeExecutor, L1Timelock with 3d delay.
- Is allowed to interact with L1Timelock - propose transactions.
- Is allowed to interact with L1Timelock - update the minimum delay of the timelock - acting via UpgradeExecutor, L1Timelock with 3d delay.
- Is allowed to interact with RollupProxy - Pause and unpause and set important roles and parameters in the system contracts: Can delegate Sequencer management to a BatchPosterManager address, manage data availability and DACs, set the Sequencer-only window, introduce an allowList to the bridge and whitelist Inboxes/Outboxes - acting via UpgradeExecutor, L1Timelock with 3d delay.
- Can upgrade the implementation of SequencerInbox, RollupEventInbox, ArbitrumBridge, ChallengeManager, Bridge, Inbox, Outbox - acting via ProxyAdmin, UpgradeExecutor, L1Timelock with 3d delay.
- Can upgrade the implementation of L1CustomGateway, L1ERC20Gateway, L1GatewayRouter - acting via ProxyAdmin 3, UpgradeExecutor, L1Timelock with 3d delay.
- Can upgrade the implementation of UpgradeExecutor, L1Timelock - acting via ProxyAdmin 2, UpgradeExecutor, L1Timelock with 3d delay.
- Can upgrade the implementation of RollupProxy - acting via UpgradeExecutor, L1Timelock with 3d delay.
Used in:
- A Multisig with 4 / 6 threshold.
- Can act on behalf of ProxyAdmin, ProxyAdmin.
- Can upgrade the implementation of ValidatorWallet, ValidatorWallet - acting via ProxyAdmin.
Used in:
- A Multisig with 4 / 6 threshold.
- Is allowed to interact with SequencerInbox - Add/remove batchPosters (Sequencers).
Used in:
A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
- A Multisig with 9 / 12 threshold. It uses the following modules: UpgradeExecutor (Central contract defining the access control permissions for upgrading the system contract implementations).
- Can act on behalf of UpgradeExecutor.
- Is allowed to interact with L1Timelock - cancel queued transactions - acting via UpgradeExecutor.
- Is allowed to interact with L1Timelock - update the minimum delay of the timelock - acting via UpgradeExecutor.
- Is allowed to interact with RollupProxy - Pause and unpause and set important roles and parameters in the system contracts: Can delegate Sequencer management to a BatchPosterManager address, manage data availability and DACs, set the Sequencer-only window, introduce an allowList to the bridge and whitelist Inboxes/Outboxes - acting via UpgradeExecutor.
- Can upgrade the implementation of SequencerInbox, RollupEventInbox, ArbitrumBridge, ChallengeManager, Bridge, Inbox, Outbox - acting via ProxyAdmin, UpgradeExecutor.
- Can upgrade the implementation of L1CustomGateway, L1ERC20Gateway, L1GatewayRouter - acting via ProxyAdmin 3, UpgradeExecutor.
- Can upgrade the implementation of UpgradeExecutor, L1Timelock - acting via ProxyAdmin 2, UpgradeExecutor.
- Can upgrade the implementation of RollupProxy - acting via UpgradeExecutor.
Participants (12):
AleksanderKryukov-CertoraDennisonBertram-TallyJohnMorrow-GauntletGoncaloMagalhaes-Immunefigzeon-OffchainLabsEmilianoBonassi-ConduitGriffGreen-GivethStevenThornton-OpenZeppelincts-Zellicfred-Arbitrumbartek.eth-L2BEATyoav.eth-EFUsed in:
Can upgrade the implementation of Validator - acting via ProxyAdmin.
Can upgrade the implementation of ValidatorWallet - acting via ProxyAdmin.
Can upgrade the implementation of ValidatorWallet - acting via ProxyAdmin.
- Can upgrade the implementation of ValidatorWallet - acting via ProxyAdmin.
- A Validator - Can propose new state roots (called nodes) and challenge state roots on the host chain.
Arbitrum Nova
Actors:
- A Multisig with 9 / 12 threshold. It uses the following modules: L2UpgradeExecutor (Central contract defining the access control permissions for upgrading the system contract implementations).
- Can act on behalf of L2UpgradeExecutor.
- Can upgrade the implementation of L2GatewayRouter, L2WethGateway, L2ARBGateway, L2ERC20Gateway - acting via L2GatewaysProxyAdmin, L2UpgradeExecutor.
- Can upgrade the implementation of L2UpgradeExecutor, L2ArbitrumToken - acting via L2ProxyAdmin, L2UpgradeExecutor.
- Can upgrade the implementation of L2GatewayRouter, L2WethGateway, L2ARBGateway, L2ERC20Gateway - acting via L2GatewaysProxyAdmin, L2UpgradeExecutor.
- Can upgrade the implementation of L2UpgradeExecutor, L2ArbitrumToken - acting via L2ProxyAdmin, L2UpgradeExecutor.
Ethereum
Escrows deposited assets for the canonical bridge that are externally governed or need custom token contracts with e.g. minting rights or upgradeability. This contract can store any token.
Implementation used in:
This contract implements view only utilities for validators.
One of the modular contracts used for the last step of a fraud proof, which is simulated inside a WASM virtual machine.
Implementation used in:
Can be used to upgrade implementation of ArbitrumBridge.
Implementation used in:
Can be used to upgrade implementation of UpgradeExecutor, L1Timelock.
Implementation used in:
One of the modular contracts used for the last step of a fraud proof, which is simulated inside a WASM virtual machine.
Implementation used in:
Can be used to upgrade implementation of SequencerInbox, RollupEventInbox, ChallengeManager, Bridge, Inbox, Outbox.
One of the modular contracts used for the last step of a fraud proof, which is simulated inside a WASM virtual machine.
Implementation used in:
Can be used to upgrade implementation of ValidatorWallet.
This contract stores the following tokens: DAI.
One of the modular contracts used for the last step of a fraud proof, which is simulated inside a WASM virtual machine.
Implementation used in:
Contract that allows challenging state roots. Can be called through the RollupProxy by Validators or the UpgradeExecutor.
Implementation used in:
Can be used to upgrade implementation of L1CustomGateway, L1ERC20Gateway, L1GatewayRouter.
Can be used to upgrade implementation of ValidatorWallet.
Escrows deposited ERC-20 assets for the canonical Bridge. Upon depositing, a generic token representation will be minted at the destination. Withdrawals are initiated by the Outbox contract. This contract can store any token.
Implementation used in:
Can be used to upgrade implementation of ValidatorWallet.
Can be used to upgrade implementation of Validator.
This routing contract maps tokens to the correct escrow (gateway) to be then bridged with canonical messaging.
Implementation used in:
One of the modular contracts used for the last step of a fraud proof, which is simulated inside a WASM virtual machine.
Implementation used in:
Can be used to upgrade implementation of ValidatorWallet.
- A timelock with access control. The current minimum delay is 3d. Proposals that passed their minimum delay can be executed by the anyone.
- Can act on behalf of UpgradeExecutor.
Proxy used in:
Can be used to upgrade implementation of ValidatorWallet.
Central contract for the project’s configuration like its execution logic hash (wasmModuleRoot) and addresses of the other system contracts. Entry point for Proposers creating new Rollup Nodes (state commitments) and Challengers submitting fraud proofs (In the Orbit stack, these two roles are both held by the Validators).
Implementation used in:
A sequencer (registered in this contract) can submit transaction batches or commitments here.
Implementation used in:
Arbitrum Nova
Router managing token <–> gateway mapping on L2.
This contract receives all SurplusFees: Transaction fee component that covers the cost beyond that covered by the L2 Base Fee during chain congestion. They are withdrawable to a configurable set of recipients.
This contract receives all SurplusFees: Transaction fee component that covers the cost beyond that covered by the L2 Base Fee during chain congestion. They are withdrawable to a configurable set of recipients.
Can be used to upgrade implementation of L2GatewayRouter, L2WethGateway, L2ARBGateway, L2ERC20Gateway.
Can be used to upgrade implementation of L2UpgradeExecutor, L2ArbitrumToken.
Value Secured is calculated based on these smart contracts and tokens:
Main entry point for users depositing ERC20 tokens. Upon depositing, on L2 a generic, “wrapped” token will be minted.
Implementation used in:
Main entry point for users depositing ERC20 tokens that require minting a custom token on the L2.
Implementation used in:
DAI Vault for custom DAI Gateway. Fully controlled by MakerDAO governance.
Contract managing Inboxes and Outboxes. It escrows ETH sent to L2.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
