 Sonic Gateway
Sonic Gateway
About
The Sonic Gateway is a token bridge built for token transfers between Ethereum and Sonic. It has a quasi-symmetrical design for two-way bridging but converts Ethereum-locked FTM into S on Sonic.
About
The Sonic Gateway is a token bridge built for token transfers between Ethereum and Sonic. It has a quasi-symmetrical design for two-way bridging but converts Ethereum-locked FTM into S on Sonic.
Funds can be stolen if
- validators allow to mint more tokens than there are locked on Ethereum, preventing some existing holders from being able to bring their funds back to Ethereum,
- validators sign a fraudulent message allowing themselves to withdraw all locked funds,
- the destination token contract is maliciously upgraded,
- a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
Users can be censored if
Principle of operation
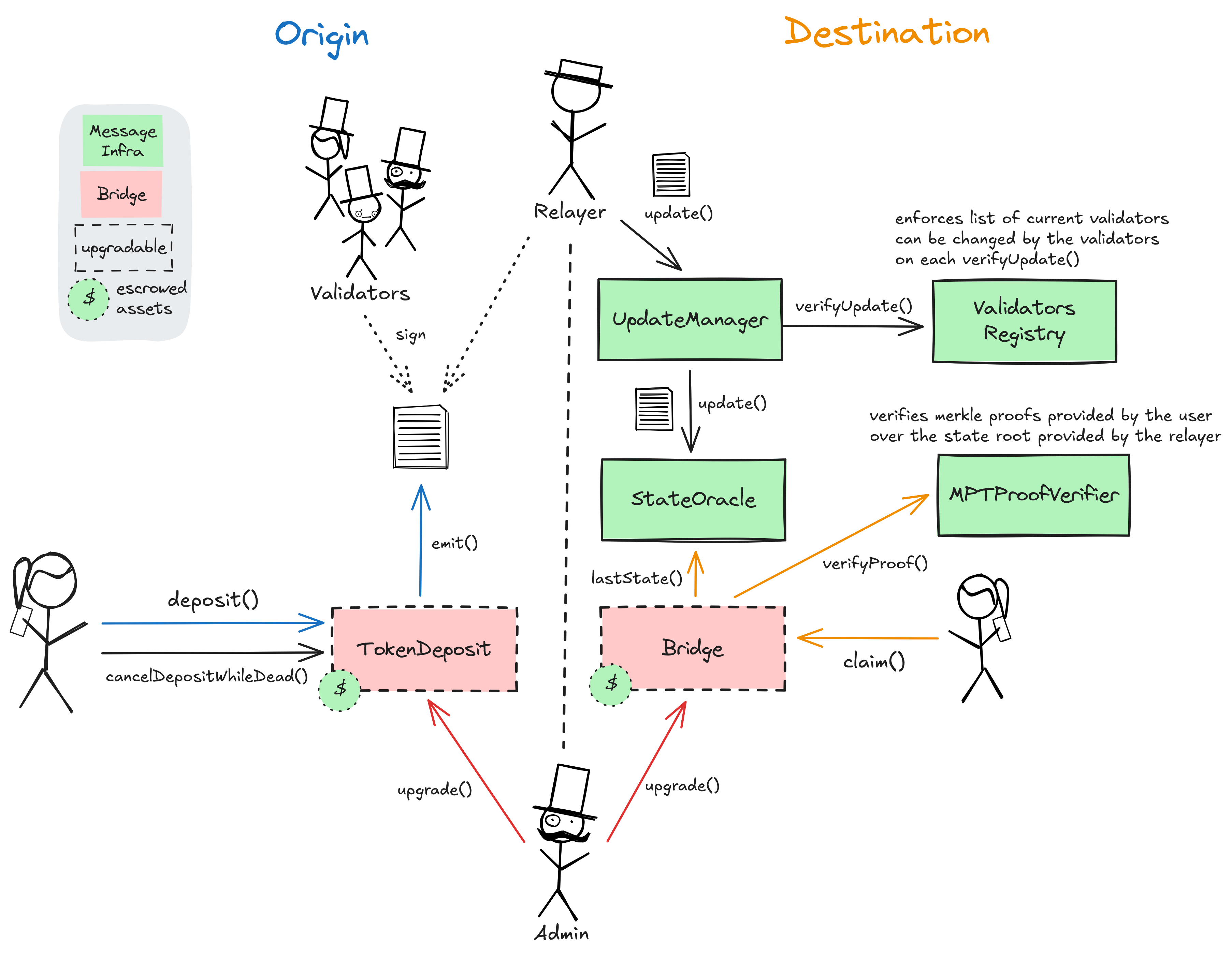
This is a standard Token Bridge that locks tokens in the escrow contract on Ethereum and mints tokens on Sonic. Permissioned relayers need to periodically update the state root in the StateOracle on both sides of the bridge. Referencing the latest state root, a user can then prove their deposit at the destination bridge contract using a merkle proof and receive their tokens. Each state root update must be signed by at least 6/8 validators. The permissioned validator set can be changed with each state update as long as it is signed by 6/8 of the current validator set.
For the special case of the S token (gas token on Sonic), there is an adapter contract on the Sonic side that escrows S and unlocks the tokens for incoming bridge transactions. The FTM token on the Ethereum side is mapped to the S token on Sonic, which means the token gets ‘converted’ when bridged in either direction. Since new S or FTM cannot be minted by the bridge, there is a limit to how much can be bridged either way. For other supported tokens, this is not the case because they can be minted on Sonic.
State updates are expected regularly (currently every 6300 Sonic blocks) and can be fast-tracked by paying a fee of 0.0065 ETH. The state updates are not enforced and only Relayers are permitted to update. The bridge has a liveness self-check that sets the bridge status to ‘dead’ after a predefined period of 200d in which no new state updates have arrived. In the ‘dead’ state, users can re-claim their deposits on the source chain side and withdraw based on the latest available state root on the destination chain side.
Transfers are externally verified
All bridge transfers are encoded in state updates that must be relayed and signed by at least 6/8 validators. These validators are unrelated to the consensus validators of the Sonic network. The validators are permissioned actors and can be changed with each state update.
Users can be censored if relayers or validators decide to stop processing certain transactions.
Funds can be stolen if validators allow to mint more tokens than there are locked on Ethereum, preventing some existing holders from being able to bring their funds back to Ethereum.
Funds can be stolen if validators sign a fraudulent message allowing themselves to withdraw all locked funds.
Destination tokens
The type of token received on the destination chain depends on the token: If it is native to this chain, the user will receive the canonical token. If the bridged token is not native to the destination chain the user will receive a minted version. The token contract in this case is called MintedErc20 and is upgradeable.
Funds can be stolen if the destination token contract is maliciously upgraded.
Ethereum
Roles:
Permissoned to sign messages (state roots) encoding transfer information or governance actions such as updates to a new validator set, which are decoded onchain with signature checks.
Permissioned to relay messages that are then verified onchain.
Actors:
- A Multisig with 2 / 3 threshold.
- Is allowed to interact with UpdateManager - set permissioned relayers.
- Is allowed to interact with UpdateManager - set the fast lane fee.
- Is allowed to interact with UpdateManager - set the number of blocks (Sonic L1 blocks) at which periodic state root updates to Ethereum are expected (heartbeat).
- A Multisig with 3 / 4 threshold.
- Is allowed to interact with TokenDeposit - set the proof verifier and the exit administrator.
- Is allowed to interact with UpdateManager - manage all access control roles.
- Is allowed to interact with TokenPairs - add tokens to the whitelist.
- Is allowed to interact with TokenPairs - manage access control roles.
- Is allowed to interact with TokenPairs - remove tokens from the whitelist.
- Can upgrade the implementation of TokenDeposit.
- Entry point for state (oracle) updates.
- Is allowed to interact with StateOracle - update the state root.
Ethereum
Registry of the current validator set. Validators can have different weights and be changed on each state update (signed by the current validators).
Verifier contract for merkle proofs.
Escrows the tokens that are bridged to Sonic. Users call this contract to deposit when bridging to Sonic, and to withdraw when bridging back to Ethereum. Since this contract escrows all tokens and defines the oracle and verification contracts, an upgrade of this contract can overwrite the logic of the whole bridge and potentially steal all funds. This contract stores the following tokens: FTM, USDT, USDC, EURC, WETH, DOLA, Silo, UNI, CRV.
Simple contract that saves the latest state root.
Token pairs are whitelisted in this contract for bridging through the Sonc Gateway.
Value Secured is calculated based on these smart contracts and tokens:
This is the central escrow that locks tokens on the Ethereum side of the Sonic Gateway.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).