 Hyperlane Nexus
Hyperlane Nexus
About
Hyperlane Nexus is a Token Bridge built on the Hyperlane interoperability protocol for cross-chain communication. The Nexus bridge validates token bridging between chains with Multisig threshold security by default, whereas the Hyperlane protocol supports... a wide range of endpoint and security configurations.
About
Hyperlane Nexus is a Token Bridge built on the Hyperlane interoperability protocol for cross-chain communication. The Nexus bridge validates token bridging between chains with Multisig threshold security by default, whereas the Hyperlane protocol supports... a wide range of endpoint and security configurations.
Funds can be stolen if
- there is no custom ISM configured and the default ISM Multisig signers submit a fraudulent transfer message,
- the token router owner changes the token router or its security stack (ISM) maliciously,
- a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL),
- the source code of unverified contracts contains malicious code (CRITICAL).
Funds can be lost if
Users can be censored if
Principle of operation
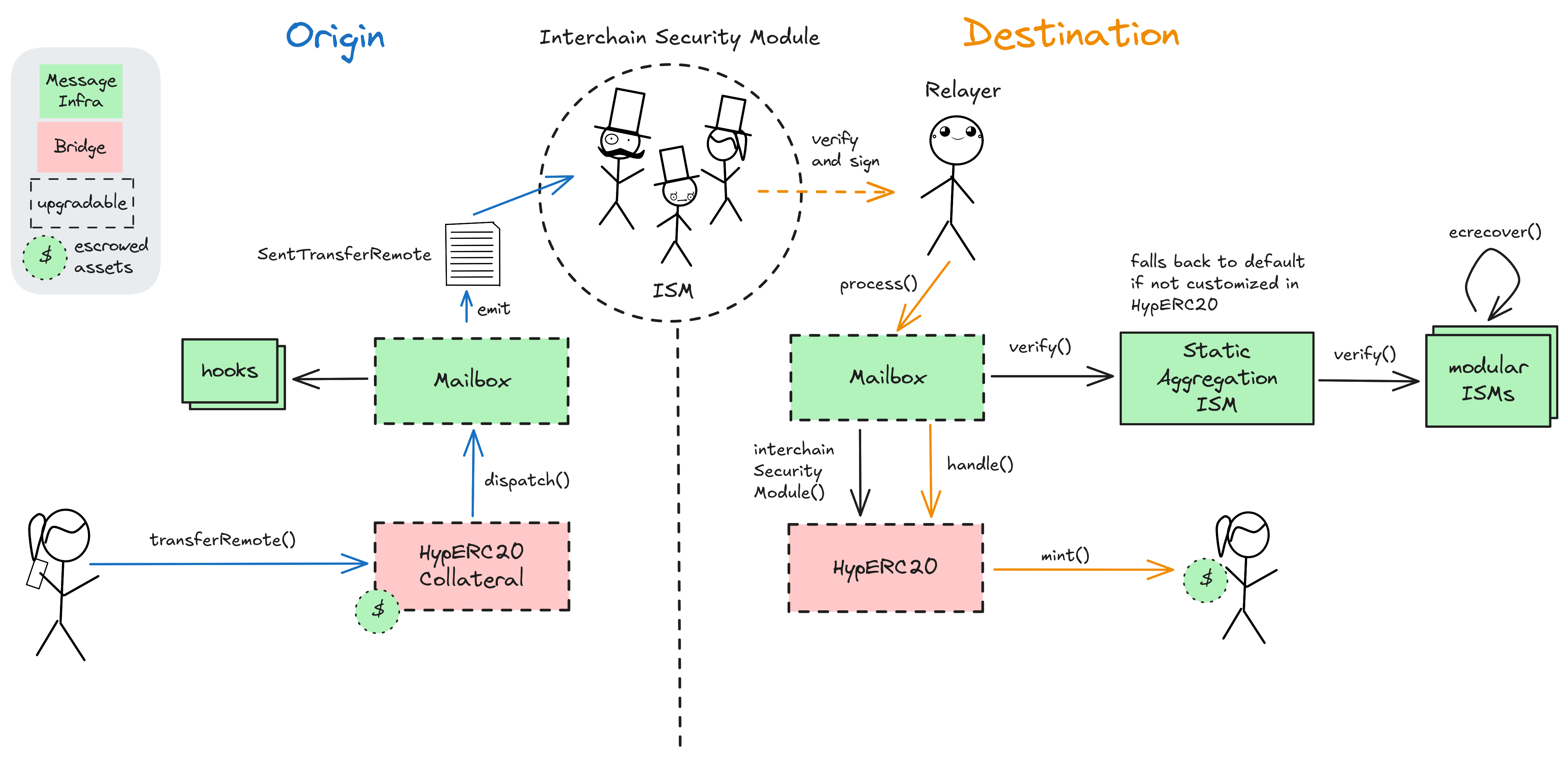
Hyperlane Nexus is a minimal Token Bridge, simply representing a certain configuration of token routers (escrows) and ISMs (verifiers) built on top of the modular Hyperlane messaging protocol. The Hyperlane messaging protocol consists of three main components: A Mailbox contract on each chain, Interchain Security Modules (ISMs), and Relayers. The Mailbox as the central Endpoint contract on each chain is used for dispatching (out) and processing (in) messages. ISM contracts define the security model (validation logic) for a given message. Unless overridden with a custom ISM config by an application or token router, the default ‘multisig’ ISM, configured by Hyperlane, is used. It validates messages by verifying that a threshold of 3 / 4 signatures from a set of validators is reached. Post-dispatch hooks on the origin chain allow for added customizability and can be verified with a synchronized ISM logic at the destination. Hyperlane security and hook configurations have chain-specifc defaults but can be customized for each token route by the router owner.
To initiate a token transfer via the Nexus bridge, users call the transferRemote() function of the Nexus bridge token router (e.g. a contract called HypERC20). Depending on the specific token router, users’ tokens may be wrapped, burned, or locked. The function call eventually dispatches a message through origin chains Mailbox, emitting a Dispatch event. Off-chain agents, such as ISM validators and Relayers, monitor the origin’s Mailbox contract and index each dispatched message. Multisig ISM validators sign off on messages by regularly producing attestations (called checkpoints), which commit to the Merkle root of all dispatched message IDs from a Mailbox at a given origin. On the destination chain, Relayers will then call the process() function on the receiving Mailbox, which verifies the relayed message with the ISM module, which is either the default Multisig ISM or an ISM configured by the destination contract owner. The Mailbox’s process() function will conclude the token transfer by calling handle() at the destination token router contract, which will contain the logic for asset delivery to the user. Depending on the application, this can be releasing tokens from an escrow, minting new tokens or other transactions.
Modular ISMs
Each crosschain transaction is emitted on the origin chain and must be picked up by relayers and verified by preconfigured verifiers (Hyperlane calls these ISMs). If they agree on a message, it is considered verified and can be executed at the destination.
Users can be censored if the required validators fail to sign the transfer message.
Funds can be lost if the required validators fail to sign the transfer message and are not actively replaced by honest ones by the admin.
Funds can be stolen if there is no custom ISM configured and the default ISM Multisig signers submit a fraudulent transfer message.
Funds can be stolen if the token router owner changes the token router or its security stack (ISM) maliciously.
Ethereum
Roles:
Permissoned to sign crosschain messages encoding transfer information, which are decoded onchain with signature checks. The validators listed here are the default validators for Ethereum and can be overridden by a custom configuration.
Actors:
- A Multisig with 4 / 9 threshold.
- Can act on behalf of ProxyAdmin.
- Is allowed to interact with DomainRoutingIsm - manage the domain -> ISM contract mapping.
- Is allowed to interact with HypERC20Collateral, HypERC20Collateral, HypERC20Collateral, HypERC20Collateral - change the ISM and hooks, whitelist new routes and update destination fees.
- Is allowed to interact with Mailbox - change the default ISM and hooks for this chain that are used for all connected contracts that do not override them.
- Can upgrade the implementation of HypERC20Collateral, HypERC20Collateral, Mailbox, HypERC20Collateral, HypERC20Collateral - acting via ProxyAdmin.
- A Multisig with 4 / 9 threshold.
- Can act on behalf of ProxyAdmin.
- Is allowed to interact with HypERC20Collateral - change the ISM and hooks, whitelist new routes and update destination fees.
- Can upgrade the implementation of HypERC20Collateral - acting via ProxyAdmin.
- A Multisig with 4 / 6 threshold.
- Can act on behalf of ProxyAdmin.
- Is allowed to interact with HypERC20Collateral - change the ISM and hooks, whitelist new routes and update destination fees.
- Can upgrade the implementation of HypERC20Collateral - acting via ProxyAdmin.
- This specific Interchain Security Module (ISM) contract is a simple ‘t of n’ module that checks that a threshold of 2 out of the [DomainRoutingIsm,UnknownIsm] ISM contracts successfully verify a message.
- Is allowed to interact with Mailbox - verify messages for destination contracts that do not specify a custom ISM.
Ethereum
ISM contract that delegates message verification to other ISMs based on the origin of the message. Currently routing to StaticAggregationIsm_eclipse for the origin Eclipse.
The source code of this contract is not verified on Etherscan.
Can be used to upgrade implementation of HypERC20Collateral.
Escrow for WBTC that is bridged from Ethereum to Eclipse. This contract stores the following tokens: WBTC.
Escrow for USDT that is bridged from Ethereum to Eclipse. This contract stores the following tokens: USDT.
Can be used to upgrade implementation of HypERC20Collateral, HypERC20Collateral, Mailbox, HypERC20Collateral, HypERC20Collateral.
Can be used to upgrade implementation of HypERC20Collateral.
This specific Interchain Security Module (ISM) contract is a simple ‘t of n’ module that checks that a threshold of 1 out of the [StaticMessageIdMultisigIsm,StaticMerkleRootMultisigIsm] ISM contracts successfully verify a message. It is an example ISM currently configured for the message origin Eclipse.
An ISM contract that verifies if a threshold of 3 validators signed a message. The validator set is immutably defined at deployment time. In addition, this ISM also verifies the presence of the given bridge message ID in a merkle tree of bridge messages. Newer validator-signed checkpoints can thus be used to verify older messages, which prevents the validators from censoring specific bridge messages.
The Mailbox contract is deployed on each chain and is used as a central Endpoint of the Hyperlane protocol to dispatch outgoing or process incoming messages.
Escrow for tETH that is bridged from Ethereum to Eclipse.
Escrow for apxETH that is bridged from Ethereum to Eclipse.
Escrow for USDC that is bridged from Ethereum to Eclipse. This contract stores the following tokens: USDC.
Escrow for weETHs that is bridged from Ethereum to Eclipse. This contract stores the following tokens: weETHs.
An ISM contract that verifies if a threshold of 3 validators signed a message. The validator set is immutably defined at deployment time.
Value Secured is calculated based on these smart contracts and tokens:
Escrow for USDC that is bridged from Ethereum to Eclipse.
Escrow for USDT that is bridged from Ethereum to Eclipse.
Escrow for WBTC that is bridged from Ethereum to Eclipse.
Escrow for weETHs that is bridged from Ethereum to Eclipse.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
Funds can be stolen if the source code of unverified contracts contains malicious code (CRITICAL).